dataPARC Security Best Practices
In today’s business environment, security of the entire spectrum of systems from individual data points to networks at large has taken on the utmost importance. dataPARC’s overall architecture as well as specific tools facilitate users’ secure access to data and information they need without compromising the organization’s IT and OT security protocols.
This document outlines best practices based on industry standards and dataPARC’s practical experience. Please use it as a set of guidelines, keeping in mind that each customer will likely require somewhat individualized configuration.
dataPARC Application Security
The following sections generally apply to the dataPARC tools that comprise the end-user interface, application server, and historian. Many of the items mentioned are part of dataPARC’s architecture or are configurable by system administrators.
User Authentication
The PARCview client and its associated tools require user authentication prior to server connection and access to any program elements. There are several options for user authentication:
Authentication Type | Identity Provider | Notes |
Anonymous | Can be set to use Capstone Built-In or custom PARCsecurity provider (named dataPARC) | No username or password required. Uses a pre-set identity to sign-in. Recommend restricting this identity’s access very tightly, or disabling this auth. type after initial installation. |
Username and Password | Can be set to use Capstone Built-In or custom PARCsecurity provider (named dataPARC) | Requires user to select Identity Provider, then enter Username and Password. Allows secure access for custom-created identities within dataPARC. |
Windows Integrated | Windows Active Directory | Uses the currently logged-in Windows User’s Active Directory ID to sign in. This adds convenience for users, but may limit identity access customization. |
Identity Providers
There are three types of Identity Providers that can be utilized by PARCsecurity:
Capstone Built-in: This type of Identity Provider contains pre-configured identities, typically used for initial installation and setup of dataPARC. For maximum user access control and auditing, it should not be used long-term.
Capstone PARCsecurity: This is a custom identity list created specifically for the customer installation. Individual user identities can be created with custom permissions for each. Identity groups can also be configured. This type offers the most flexibility and security, but does require the user to enter a username and password if not configured for automatic sign-in. This Identity Provider allows password options such as expiration based on age, requirement to change password on first login, and requirement of complex passwords. This increases security and allows compliance with local password policies.
Windows Active Directory: The identity list is provided by the domain’s Active Directory.
Public: If “Public” is NOT checked in the dataPARC UA Security console, the user may only log-in with the currently logged-in Windows User Active Directory ID. This is considered the most secure login method, but limits identity customization. If “Public” IS checked, all AD user identities are exposed, allowing a user to sign-in to PARCview with a different identity than the current Windows user.
Virtual: This identity type can be configured to allow only identities which have been explicitly added to the list of PARCsecurity identities, OR it may be set to allow “virtual” identities (those that exist within AD, but have not been added to the PARCsecurity list). These will inherit group permissions (“Everyone” and any AD groups to which they belong). Allowing “virtual” identities reduces the effort involved in adding new users, but increases risk since access is not specifically managed at the PARCsecurity level.
Identities
dataPARC user identities should be configured with the maximum possible level of granularity. Sharing of identities should be eliminated if possible – including at shared workstations such as control rooms and Lab benches. Providing individual identities for each user will ensure permissions are correct and that audited events are recorded correctly.
Groups
Permission configuration within dataPARC can be simplified by establishing identity groups. Group permissions can be customized, and all identities added to the group will inherit its permissions. Groups can also be added to groups, creating a permission hierarchy.
Permissions
Permissions can be set for each group and identity at both the application and tag level. Each group or identity should be provided “Allow” access to only those applications and tags needed to perform their work. Note that tag permissions can be set by location, source, process area, and individual tag. This can simplify permission configuration.
Security Profiles
A set of configured permissions is saved as a Security Profile. Three initial profiles are provided, but each customer should create at least one custom profile for each site.
Default: This is typically the starting point for each location’s custom permissions configuration. It initially contains a set of pre-configured permissions for the Everyone group, which are inherited by all identities. No identities are pre-configured for this profile, so either new identities must be created within a PARCsecurity or Microsoft Active Directory identity provider, or the pre-configured identities from the other initial security profiles may be used. If no new identities are created or configured, users can only sign in anonymously or with the built-in Administrator identity.
In this security profile, the Everyone group has the Allow with Inheritance tag access permission on the default Location.
Everyone (Default):
· Launch PARCmobile
· Allow Access Outside Displays Directory
· Launch PARCview
· Launch PARCview Web
· Read Data Series Tag List
· View Computer Directory Tree
· Windows Explorer Access
PVbasic: The PVbasic security profile has permissions configured for a set of group identities that correspond to the pre-7.0 password system. This makes it useful for those upgrading a pre-7.0 dataPARC installation that was utilizing individual passwords for access to various tools.
This security profile also has permissions configured for the Everyone group, which are inherited by all identities. However, the Everyone group has no access to tags. Make sure to assign tag permissions before activating the profile.
Everyone (PVbasic):
· Launch PARCgraphics Designer
· Launch PARCmobile
· Allow Workflow Edit
· Allow Workflow Schedule
· Allow Access Outside Displays Directory
· Launch PARCview
· Launch PARCview Web
· Operator Target Edit
· Read Data Series Tag List
· View Computer Directory Tree
· Windows Explorer Access
PV_AlarmConfig:
· Alarm Configuration
PV_AlarmEventAudit
· Allow Alarm Event Deletes
· Allow Alarm Event Edits
PV_CalcScript:
· Calc Builder
PV_LimitGradeConfig:
· Grade Maintenance
· Grade Specification
· Limit Calculation
· Limit Configuration
PV_MDEConfig:
· MDE Configuration
PV_PARCsuiteConfiguration:
· dataPARC Admin
· PARCview Configuration Admin
PV_ReportDesigner:
· Launch Report Designer
· PARCReport Configuration
PV_TracSuite_PARCmodel:
· Configure TracSuite
· Launch PARCmodel
UAbasic: This security profile has permissions configured for four user groups: Administrators, Operators, Power Users, and Everyone. The Power User group is a member of the Operators group, meaning all permissions of the Operators group are inherited by the Power User group (in other words there is no permission an Operator could have that a Power User could not). Pre-configured permissions for the Everyone group are inherited by all identities.
In this security profile, the Everyone group has no access to tags. Make sure to assign tag permissions before activating the profile.
Everyone (UAbasic):
· Launch PARCmobile
· Allow Access Outside Displays Directory
· Launch PARCview
· Launch PARCview Web
· Read Data Series Tag List
· View Computer Directory Tree
· Windows Explorer Access
UA_Admin:
· Granted access to all roles
UA_Operator:
· Allow Alarm Event Edits
· Operator Target Edit
UA_PowerUser:
· Launch PARCgraphics Designer
· Launch Report Designer
· PARCReport Configuration
· Allow Workflow Schedule
· Alarm Configuration
· Allow Alarm Event Deletes
· Allow Alarm Event Process Edits
· Calc Builder
· Launch Asset Manager
· Launch PARCmodel
· Limit Calculation
· Limit Configuration
· Logbook Edit
· MDE Configuration
· MDE Header Template Configuration
· MDE Lock Record
dataPARC Server-Client Communication
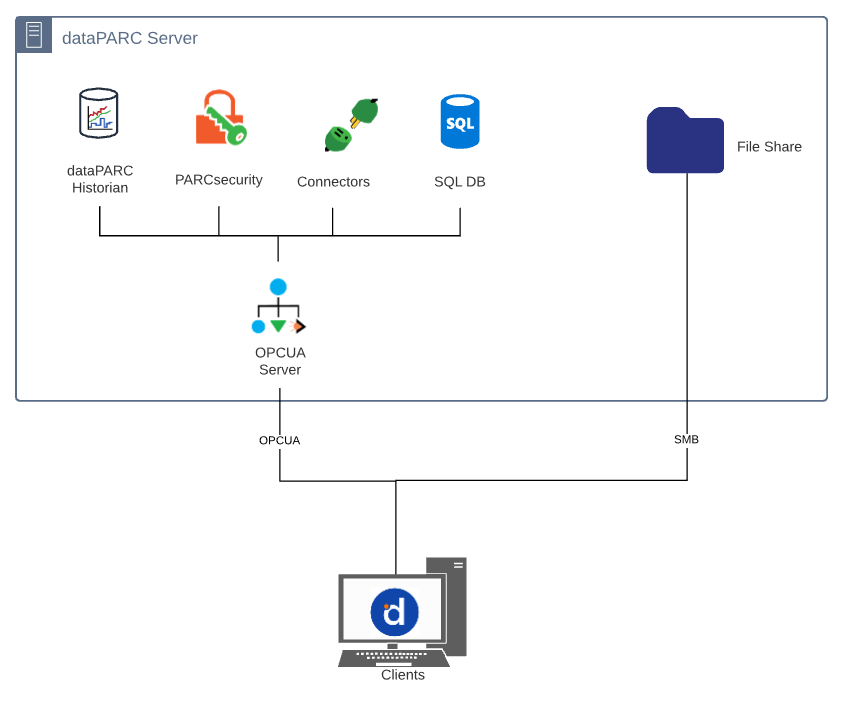
OPC-UA
The PARCview client and associated tools communicate with the dataPARC server via the OPC-UA protocol.
Key Concepts
- OPC-UA uses a single TCP port. This allows it to work well with a standard packet-filtering firewall.
- PARCview does not directly connect to the SQL Server (unless a DSN is defined in Site Connection Configuration)
- Certificate exchange is used to set up a secure channel. It uses basic 128 encryption.
- User credentials set access to application functions (open PARCview, see specific tag, etc).
Reference Documents
dataPARC Server-SQL Database Communication
Key Concepts
- TLS 1.2 protocol is utilized. Cryptography more secure than legacy SSL methods.
- Capstone recommends setting database access to lowest level of privilege needed for each database. “db_owner” access only needed for major software upgrades, and can be rescinded for normal usage.
Recommended Database Permission Table
Description | Permission | |
ctc_config | Main repository for dataPARC applications | db_datareader and db_datawriter |
ctc_security | Stores all security configuration | PARCSecurityAdminRole |
ctc_gds | Global discovery service for authorization and certificate management | db_datareader and db_datawriter |
File Transfer (SMB or Display Service http)
SMB
Access to PARCview display files can be provided via Microsoft SMB, which allows encryption between the dataPARC Server file share and the PARCview client.
Key Concepts
- File/Folder permissions based on logged-in user.
Reference Documents
Display Service http
PARCdisplay Service allows dataPARC Displays to be accessed through a web-based service instead of from a shared network folder. This method is less secure than SMB.
Key Concepts
- Display Service currently does not support identity-based access control
- File transfer via the Display Service is currently not encrypted
Data Collection Security
At customer sites with the dataPARC Historian, Capstone’s PARCIO application reads data directly from real-time sources before transmitting it to the Historian itself. PARCIO is also known as the “data collector”. The most common data collection protocols are OPC Classic (OPCDA, OPCHDA) and UPC-UA.
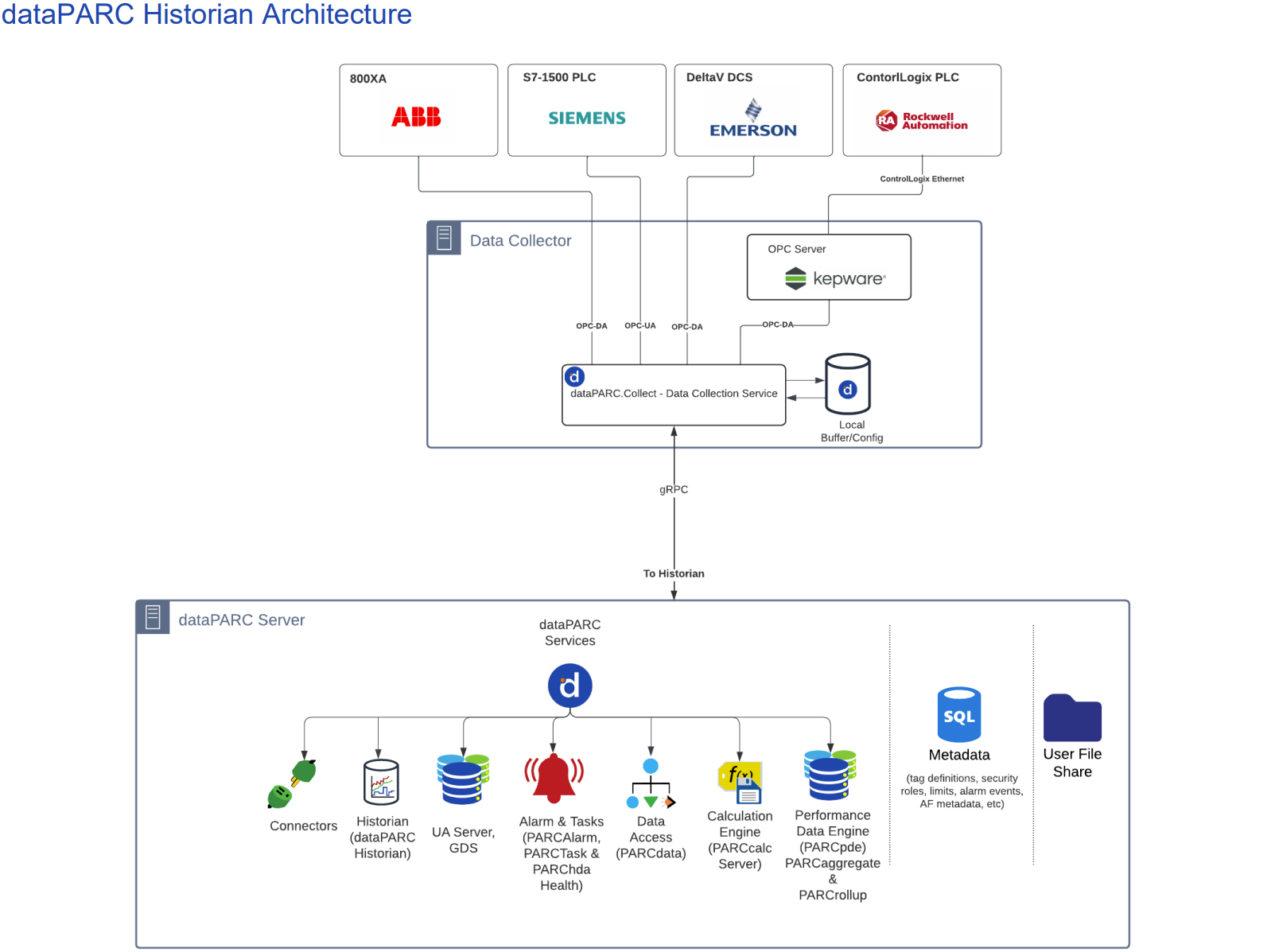
OPC Classic (OPCDA, OPCHDA)
The OPC Classic protocols should only be used if the source OPC Server does not support OPC-UA. This is the case with many legacy data sources.
Key Concepts
- OPC classic protocols rely on dynamic port ranges and should not be used across a standard packet-filtering firewall.
- Microsoft recently found vulnerabilities in DCOM (typically required for OPC Classic connections from one PC to another). Capstone recommends to either run remote data collection using RPC_C_AUTHN_LEVEL_PKT_INTEGRITY level or install services on the same computer as the OPC server.
- It is also recommend to run data collection as a service with a Windows service account defined specifically for the data collection (as opposed to using system account). This allows the specific user’s permission to be tailored to the lowest level of permission needed.
- Do not use a default password for this service account.
Reference Documents
OPC-UA
OPC-UA is the modern standard protocol and should be used whenever possible for data collection.
Key Concepts
- OPC-UA uses a single TCP port. This allows it to work well with a standard packet-filtering firewall.
- Certificate exchange is used to authenticate connections and to encrypt messages. OPC server dictates encryption level. Recommend setting server to sign and encrypt with Sha256.
- User credentials are used to set access to specific tags and functions (e.g. read/write to tag). It is recommended that the server not allow anonymous connections and to use a specific user for the data collection. Do not use a default user/password.
Reference Documents
gRPC
At sites using the dataPARC Historian, both the data transfer between the individual source data collectors and the Historian and between the Historian and other dataPARC Tools is based on the gRPC protocol.
Key Concepts
- gRPC uses a single TCP port. This allows it to work well with a standard packet-filtering firewall.
- All gRPC traffic will be encrypted starting with dataPARC version 7.3.
Reference Documents
Audit Trails
If users are logged-in with individual identities, dataPARC’s powerful auditing capabilities can provide valuable insights for system administrators. All audited events will include a record of the associated user identity.
Functions with User-Level Auditing
- Alarm Configuration
- Alarm Events/Causes
- Manual Data Entry
- Logbook Entries
- PARCIO Source Configuration (indicates last user to modify)
Functions with Change or Comment-based Auditing
- PARCtask Workflow Template Configuration
- Alarm e-mail Template Configuration
- Grade Versions – comments can be added
- Limits Specifications – “change notes” can be added
- Source and Process Tag Configuration – created and modified timestamps recorded
General Windows Server Hardening
dataPARC’s architecture affords the customer full ownership of all hardware, data storage, application environments, etc. Thus, customer organizations are free to configure server systems to meet internal security policies. Capstone does make the following general recommendations:
User Configuration
Establish the minimum number of required users with the minimum permissions necessary to access and maintain dataPARC Server functions. Enforce a strong password standard and account lockouts on multiple consecutive login failures.
Windows Features and Roles
Uninstall unnecessary components and remove unneeded user roles to simplify maintenance and reduce potential security risks.
Frequent Patches
Follow a schedule for frequently installing operating system and software component patches, especially those provided to address security concerns.
Firewall Configuration
Set up firewalls with only the necessary ports open for specific required data and/or file transfer. This is especially important for connections between Operations/Process Control networks and Business/IT networks.
Service Accounts
Add specific user accounts for services, providing only the permissions necessary for operation of each individual service.
